FAQ
Why should I use an SS11 sensor instead of just using the internal smartphone's Wi-Fi scanner ?
Wi-Fi analyzers based on Android smartphones were very popular in the past. Unfortunately they suffer from several limitations that, as long as newer Android versions are released, are becoming more and more severe up to the point of making the internal scanner pretty unusable for such kind of applications. SS11 overcomes such constraints allowing your smartphone to emulate a professional Wi-Fi scanner/sniffer. Here are some of SS11 key factors:
- No scan throttling issues
- No location permission requested
- RSSI accuracy independent from host smartphone
- Customizable scan rate interval
- Single channel mode
- Sniffer mode (management/data frame capture)
What about LOCATION permission ?
Starting from Android 6.0 (API 23), in order for applications to use Wi-Fi scanning, the ACCESS_FINE_LOCATION or ACCESS_COARSE_LOCATION permission is mandatory. Besides, you need to make sure the location service in phone settings is turned on, otherwise a Wi-Fi scan will return an empty list of networks. If this sounds like a threat to your privacy, here is a good news; SS11 doesn't require any location permission to work.
What about Android 9 restrictions ?
Starting from Android 9.0 (API 28) Google has introduced a further restriction that allows each foreground application to scan Wi-Fi a maximum of 4 times per 2 minute period (scan throttling). This limitation make it impossible for an app to act as a real time analyzer. SS11 is not affected by scan throttling; it can perform a complete scan in about a second or it can check beacons during single channel mode at 10x higher rates.
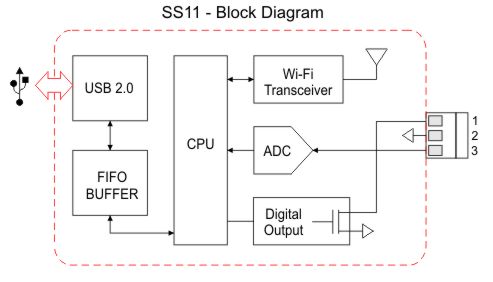
Can I use an SS11 as a stand-alone device ?
Yes, in this case you can supply the sensor through a standard USB 5V charger and make use of SS11 terminal block to drive an external actuator. The function of the SS11 output is customizable by programming its internal non-volatile memory directly with your smartphone.
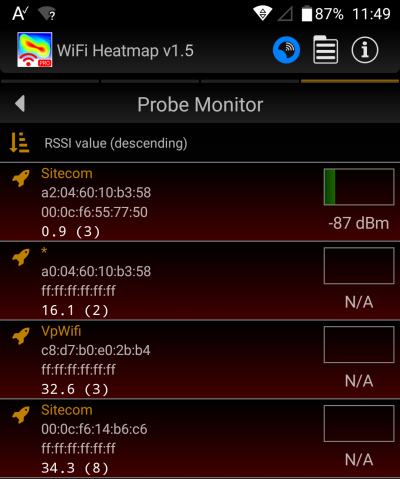
What can I do by running SS11 in sniffer mode ?
When SS11 runs in sniffer mode, it captures packets in the air without connecting with any Access Point. Particularly, it can capture probe requests that are packets continuously broadcasted to the air by smartphones, printers, laptops and IOT devices. As you can track a nearby device by its unique MAC address, you could exploit this feature for some useful applications. For example, you could trigger a particular event when SS11 detects your smarphone or when an unauthorized MAC address is captured.